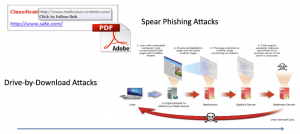
What is Ransomware?
What is ransomware? – A type of malicious software (Malware) which restricts access to a computer and/or the files on a computer until a ransom amount is paid.
It’s something that is downloaded via email or file from the internet or passed between users much the same as a virus, this can be linked to a virus, malware, Trojan horse these are the same thing but a more evolved version.
What is it going to do to a single computer or network? – it’s going enforce restrictions through encryption and prohibit access to certain areas of a machine or an environment once infected.
Remediation – How do we fix this mess if hit?
Well you either pay the money and even then, there is no guarantee that the newly encrypted data from the ransomware attack will even be decrypted and useable again.
Or and this is the sweet spot – Restore that compromised data from backups.
Mitigation
Firstly, it’s an education thing educating the work force and the IT admin teams, if a corporate company gets attacked, it’s a huge CV generating incident and they are probably going to be released of their duties as soon as they have fixed the mess.
Second is going to be the audit process of checking on a routine basis that permissions within the environment are up to scratch and that people do not have access to files and shares they shouldn’t. “Cryptowall” (A type of ransomware) will encrypt to the level of the user.
Third we have the updating of systems, patch Tuesday keep the Operating Systems and application software up to date, there are releases all the time around preventive patches that are going to keep vulnerabilities at bay just by adhering to this step.
And finally, Backups, Backups, Backups. Make sure pertinent data is backed up and preferably NOT accessible to the standard user!
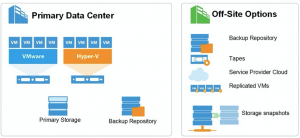
3-2-1
At Veeam we speak about the 3-2-1 as a methodology every single day in regards to protecting data and allowing you to address nearly any failure scenario. The great thing is it also doesn’t require any specific technology. (regardless of vendor, this should be followed as any Backup, Business Continuity and Disaster Recovery methodology)
Running workloads “count” as one copy. The other two is where you need to think a bit….
This is an old picture from El Rickatron but still so relevant for this story.
Back to the threat of ransomware, the real saving point is making sure you have a copy of your data on “offline storage” but what is offline storage. All the Off-Site options could be deemed in a way a level offline but I think a few other attributes would be:
- Out of band communication
- Protocol reliance
- Traversal of authentication mechanisms
Infrastructure Security
I think this goes with the remediation section but this is where we can advise our customers on how to prevent this from happening to them even with a Veeam solution in place.
- Access Rights – specific user permissions and security on files and shares allowing only access to the required individuals, this should mean any backup target from a Veeam perspective.
- Anti-Virus Software – the last thought when deploying workloads but it’s so important and always has been, we also need to be careful here as some on access scanning AV will stop or slow down the Veeam backup process.
- Segregated and Dedicated Networks – being able to separate or isolate the “Backup” network from the production network is going to increase the chances of being hit by something.
EndPoint
Or soon to be Agent for Windows will also have a play here from a preventive perspective. I would hope most of you guys are running Veeam Endpoint Backup on your personal and work computers to protect those workloads and data. (it would look bad working for Veeam and you lost some data!)
The common misconception that cloud based storage is exempt from ransomware is just not true. DropBox, OneDrive and all the other options out there have as much vulnerability as any other storage option. The moment something changes in your cloud storage maybe an update of a spreadsheet it will instantly be updated within the cloud storage. If the file is hit locally with a ransomware virus, then it’s pretty much going to be replicated up to the cloud storage also.
All the same preventive techniques apply to your home PC to your data center workloads when it comes to ransomware, access rights, offline copy of your backup and adhering to that 3-2-1 methodology.
Other Resources
I also wanted to add some additional resources that cover different areas of this threat,
https://www.veeam.com/blog/how-to-protect-against-ransomware-data-loss-and-encryption-trojans.html
http://windowsitpro.com/blog/ransomware-backups-and-offline-storage-oh-my
https://www.veeam.com/executive-blog/ransomware-survey.html
Thanks for reading and hopefully this was a useful 101 on the fundamentals of Ransomware, but also how Veeam can assist you in the prevention of being hurt badly by this movement.