A few months back I touched on a cool new capability within Veeam Backup & Replication called Location tagging allowing administrators to mark the location of their physical constructs. This in turn can be used for GDPR and data locality but also other rules and regulations a company may have to adhere to.
This post will go into the capabilities that this then extends to Veeam ONE in terms of being able to report against these locations and more importantly be able to highlight location violations that may have occurred within the company.
At the same time Veeam Backup & Replication was updated to update 3 so was Veeam ONE.
In the post linked above that covered this feature within backup and replication I talk of the benefits of being able to define where workloads reside in their backup state. This is good but it’s not that useful when you get to scale if you don’t have a way of reporting against those workloads.
Veeam ONE Reporter
Veeam ONE Reporter is one of the three components that come with the Veeam ONE product, it allows for the data that is captured via the monitor to be pushed into neither dashboard for instant visibility or to reports that can be scheduled and sent to various areas of the business. It is the reporter component that we will use to gain our visibility into the data location tagging we achieved in Veeam Backup & Replication

To begin with a bit more of an overview to reporter, there are already lots of really great reports built into the product that can be used out of the box, the ability to see change tracking reports to see who has made changes to your virtual environment as well as your backup. There is a report on Active Snapshots, in that VMware world you are going to be treading or walking a thin line by keeping many active snapshots open for a period of time.
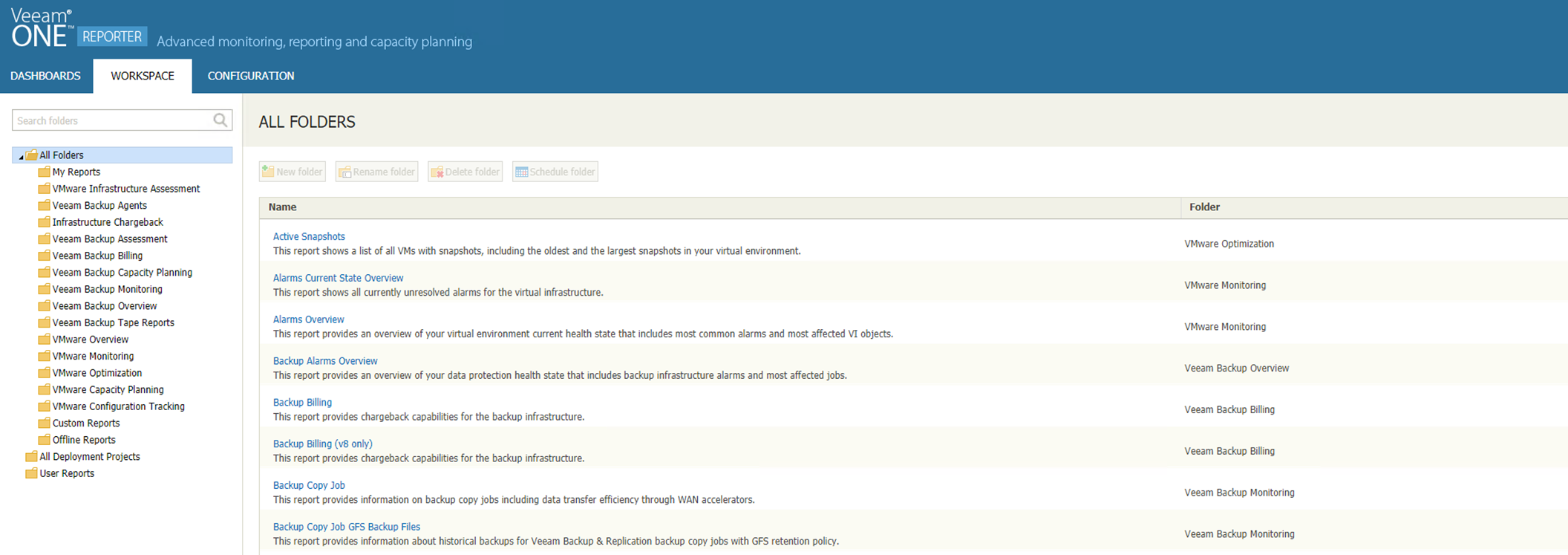
There is also the ability to create custom reports where you can take the useful bits of other reports and include that information into one custom report.
For the purposes of seeing how we can benefit from the data locality tagging there are two reports, and these are searchable in this same screen above over to the right of the screen.
Data Sovereignty Overview
When you select this report, you are faced with two options, scope of the environment we want this report to be ran against. Could be multiple sites, virtual centres etc different data protection or security officers with different responsibilities or even different countries or continents.
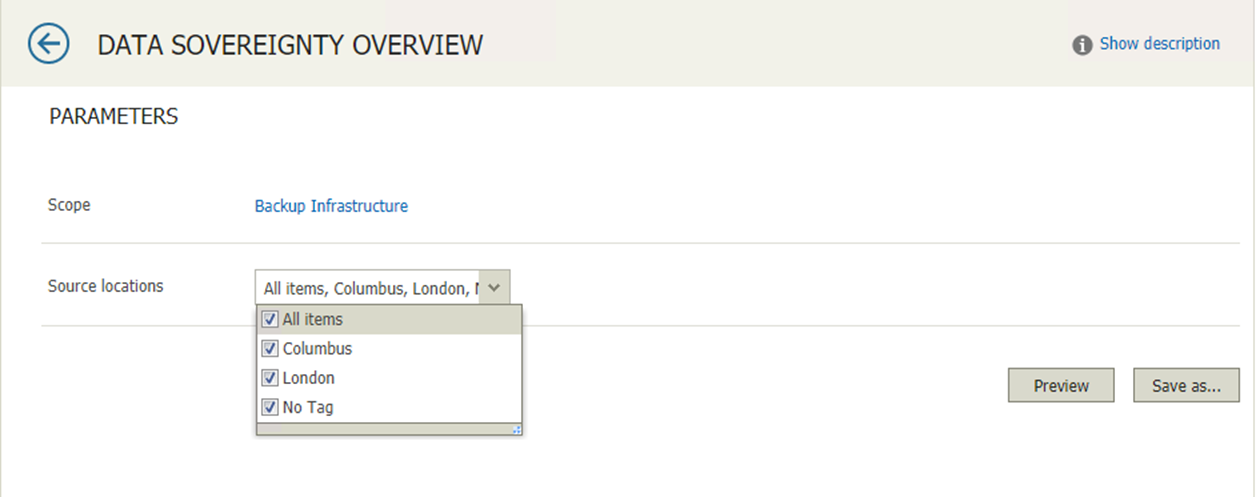
As you can see secondly you then can choose what are those source locations that we want to include. These are the locations that were created within Veeam Backup & Replication.
You can then run that there and then or we can save and configure a schedule.
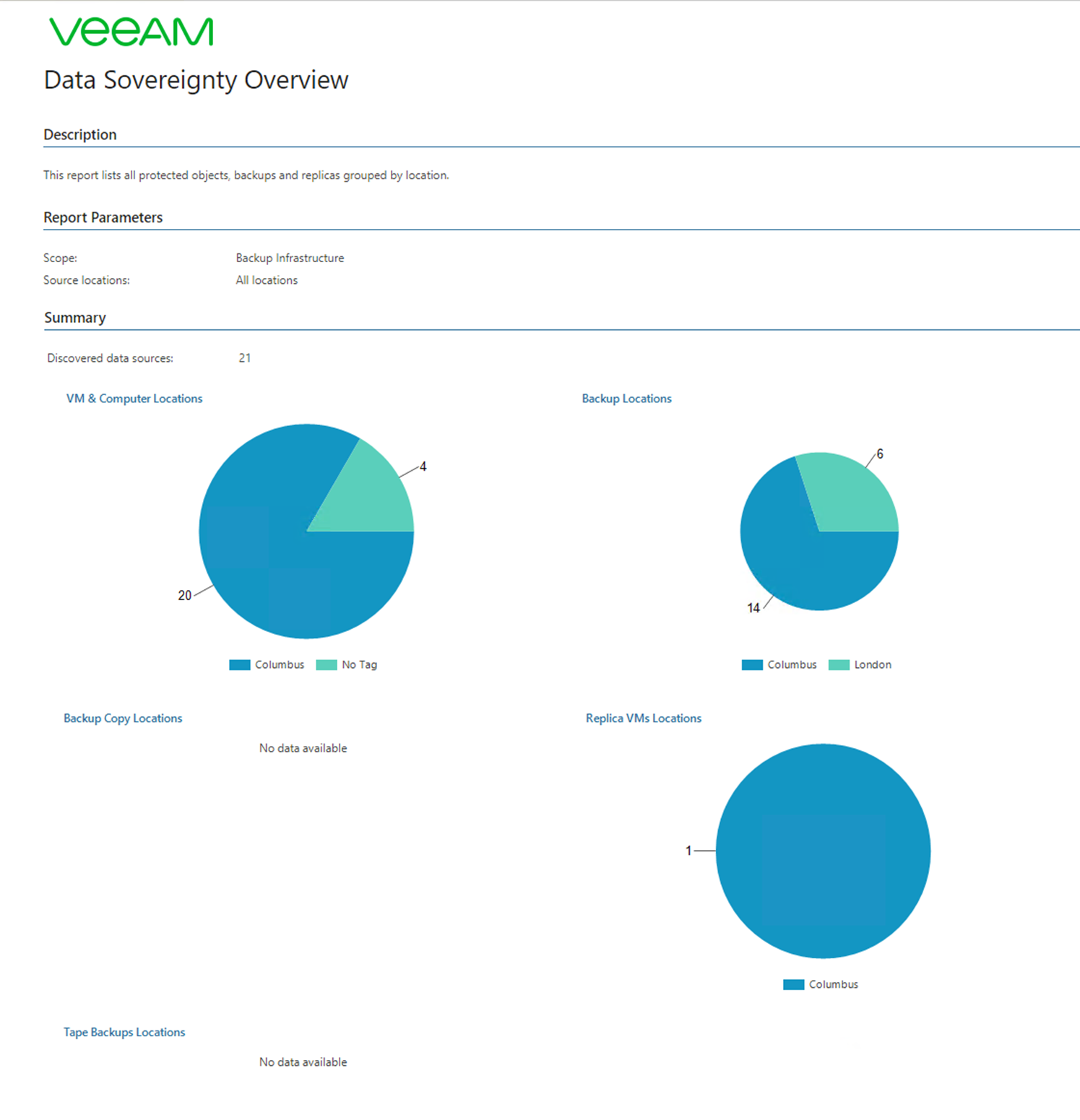
The first page of the report is going to show us Virtual Machines or Agent Locations, we can see from this report that I have 4 machines that do not contain a tag at all, we also see the backup locations in our environment we have two locations both defined as Columbus and London. Other information such as Replica locations and tape drive locations can also be configured.
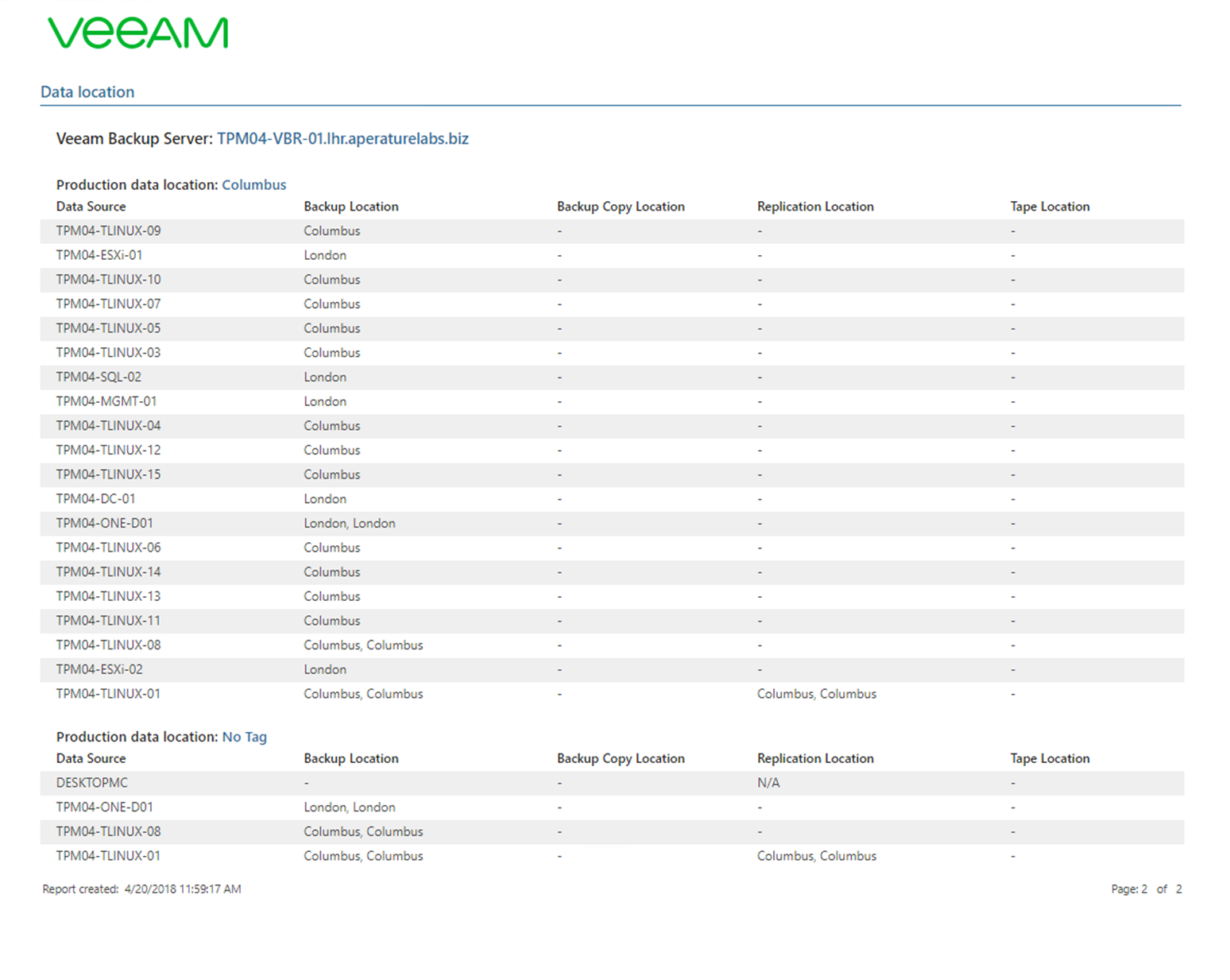
The second page and this page can be exported into a Word, Excel or PDF file at this stage. Here we can see the backup location if there were additional or secondary long-term retention backup copies we can see where this data now resides. For an overview report that you might want to see every now and again to make sure that workloads were being marked as being in a location it’s quite a powerful feature. As well as being very simple and easy to run and gain that information.
Data Sovereignty Violations
The more important report that I expect to be ran more frequently would be the Data Sovereignty Violations report. This is going to take those locations and it’s going to now look at where the data is residing and report back any violations of data sovereignty, this will really help if your business is spanning multiple geolocations and you have to have visibility into not only production data but also the backup data.
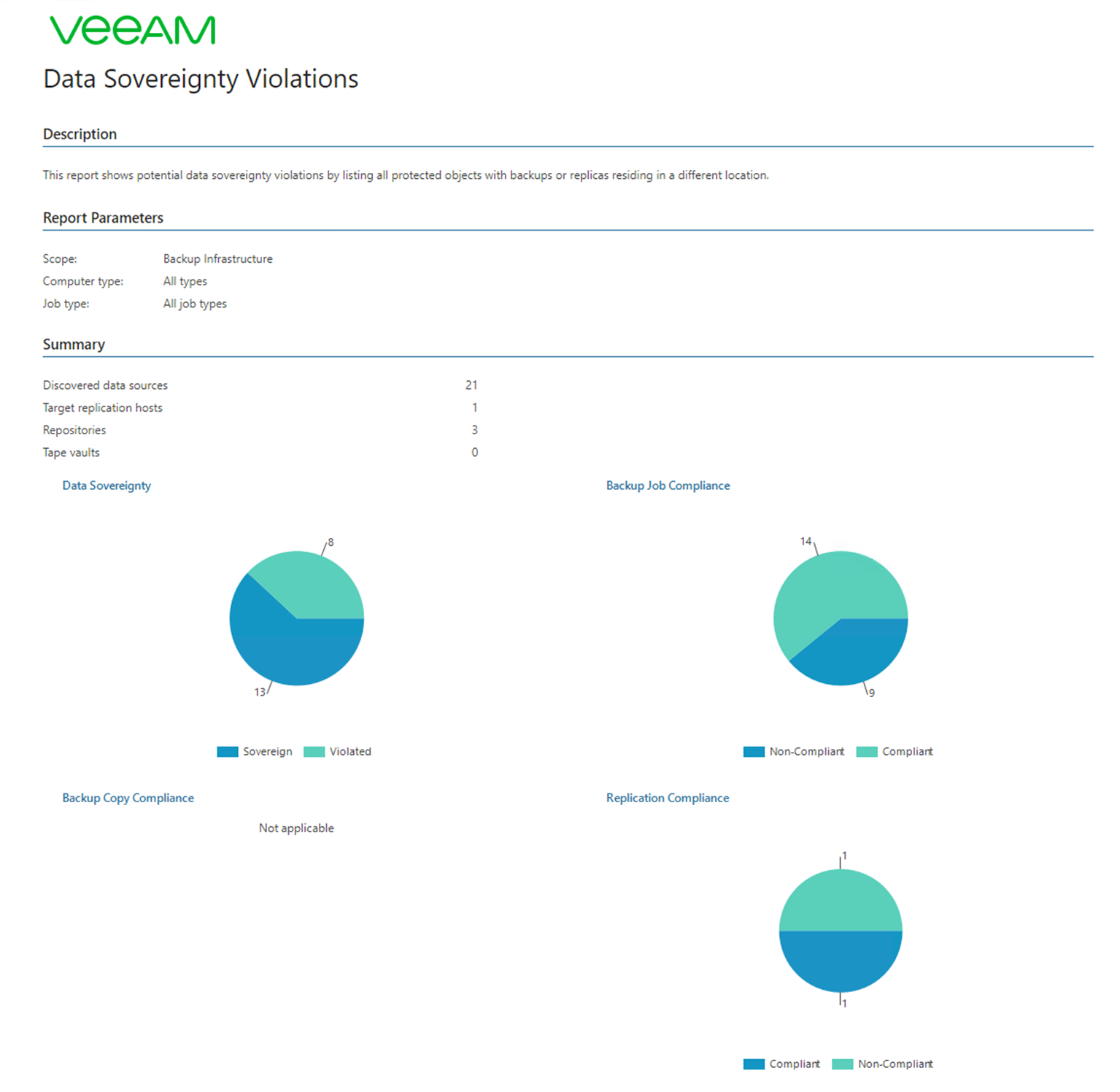
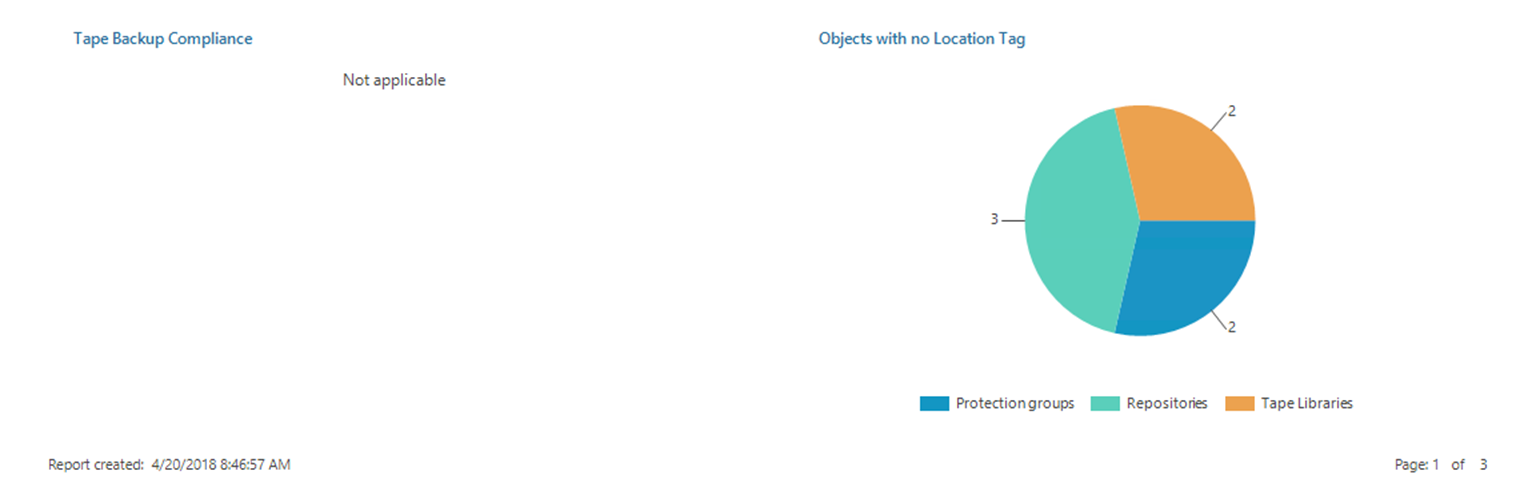
This first page or the first snapshot gives you a good first view of where there are possible problems with regulations. If it is with backup jobs, replication jobs or even tape, it will also high light where no tag has been defined on certain constructs within Veeam Backup & Replication.
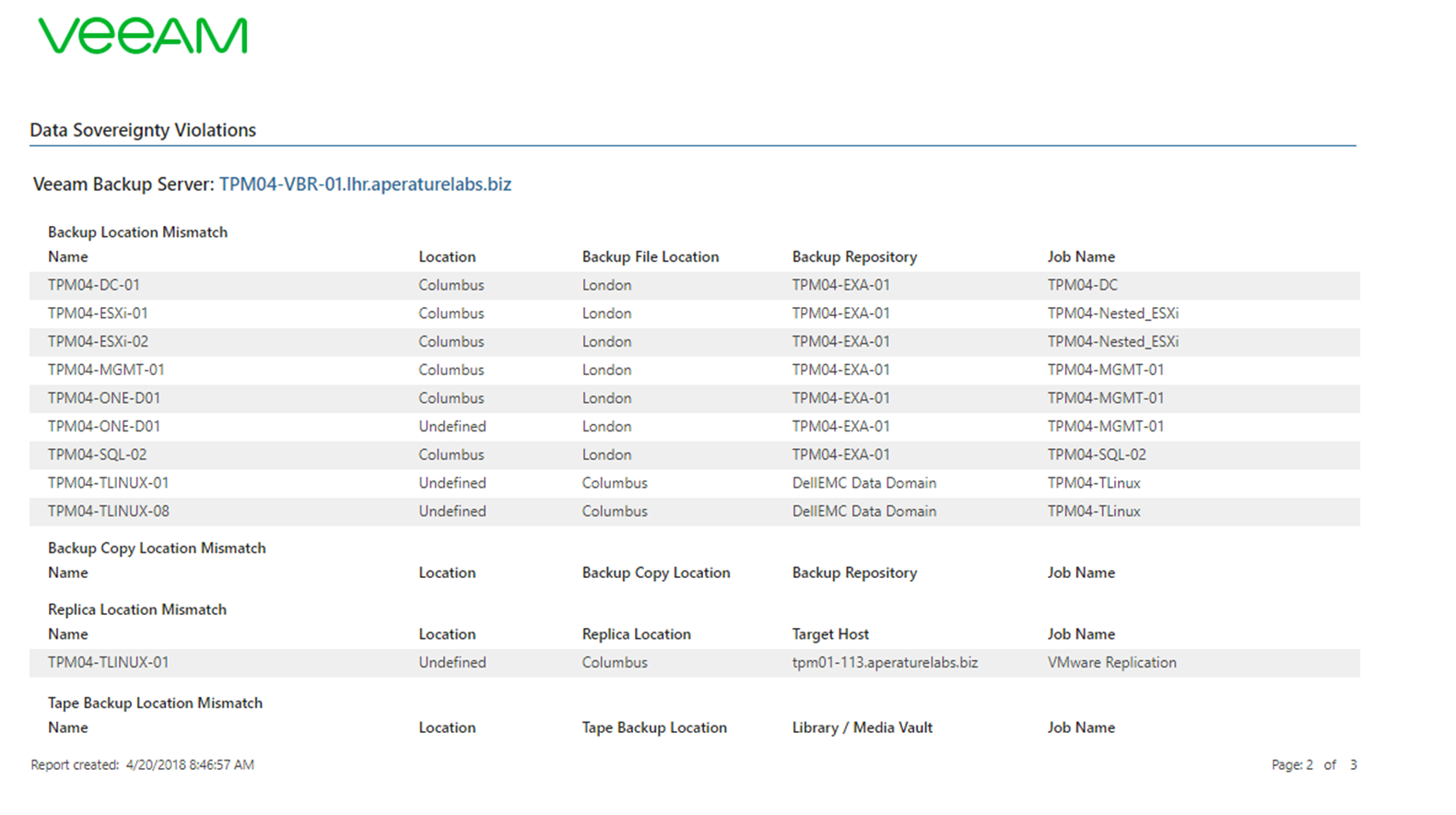
The second screen is going to drill down into more detail about where the live system is running but tell us where the backup is residing. If this is different than expect to see the mismatches or violations in here.
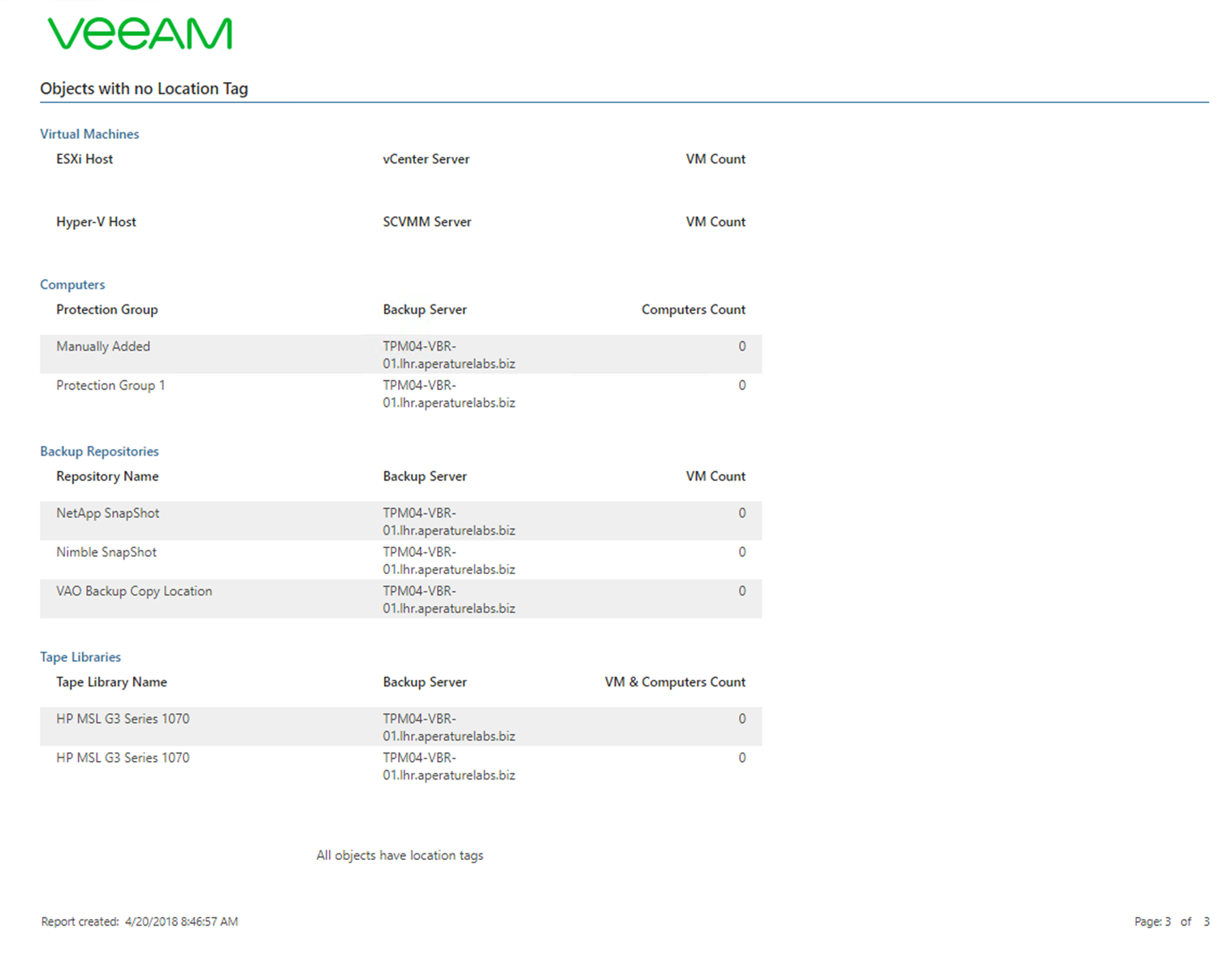
The final page is going to highlight those constructs that do not have a tag assigned to them.
Finally I wanted to share those example reports in PDF format just to see what they look like.
